Sentinel finds flaws in Microsoft Azure Defender for IoT
- April 6, 2022
- Steve Rogerson
Sentinel Labs has discovered a number of critical security flaws in Microsoft Azure’s Defender for IoT affecting cloud and on-premise users.
Unauthenticated attackers can remotely compromise devices protected by Microsoft Azure Defender for IoT by abusing vulnerabilities in Azure’s password recovery mechanism.
Sentinel Labs’ findings were proactively reported to Microsoft in June 2021 and the vulnerabilities are tracked as CVE-2021-42310, CVE-2021-42312, CVE-2021-37222, CVE-2021-42313 and CVE-2021-42311 marked as critical, some with CVSS score 10.0.
Microsoft has released security updates to address these critical vulnerabilities. Users are encouraged to take action immediately. So far, Sentinel Labs has not discovered evidence of in-the-wild abuse.
Operational technology (OT) networks power many of the most critical aspects of society. However, many of these technologies were not designed with security in mind and can’t be protected with traditional IT security controls. Meanwhile, the IoT is enabling a new wave of innovation with billions of connected devices, increasing the attack surface and risk.
The problem has not gone unnoticed by vendors, and many offer security in an attempt to address it, but what if the security itself introduces vulnerabilities? The Sentinel report discuss critical vulnerabilities found in Microsoft Azure Defender for IoT, a security product for IoT and OT networks from Microsoft Azure.
It shows how flaws in the password reset mechanism can be abused by remote attackers to gain unauthorised access. Then, it discusses multiple SQL injection vulnerabilities in Defender for IoT that allow remote attackers to gain access without authentication.
The research raises serious questions about the security of security products themselves and their overall effect on the security posture of vulnerable sectors.
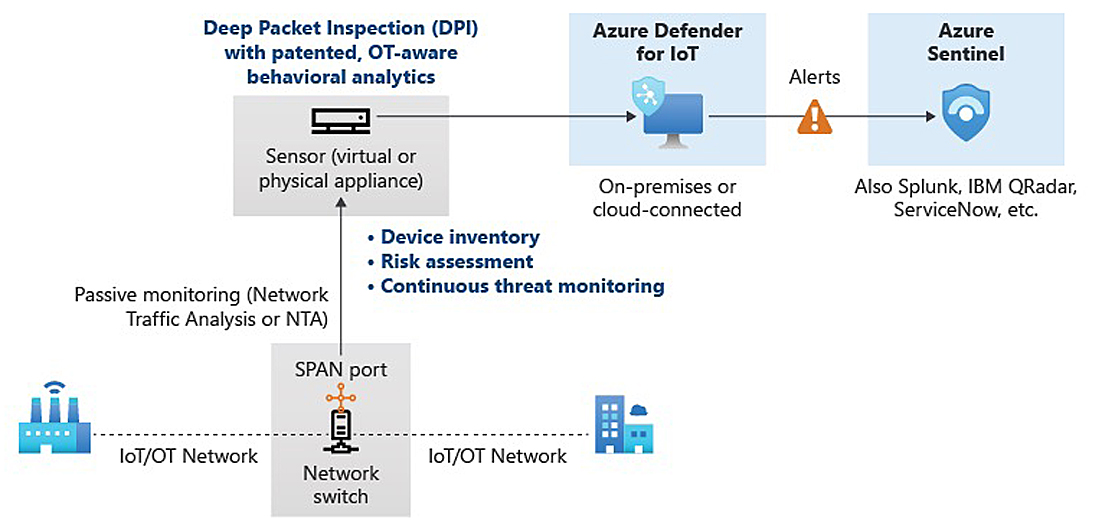
Microsoft Defender for IoT is an agentless network-layer security for continuous IoT and OT asset discovery, vulnerability management, and threat detection that does not require changes to existing environments. It can be deployed fully on-premises or in Azure-connected environments.
This consists of two main components. Microsoft Azure Defender for IoT Management enables teams to manage and analyse alerts aggregated from multiple sensors into a single dashboard and provides an overall view of the health of the networks. Microsoft Azure Defender for IoT Sensor discovers and continuously monitors network devices. Sensors collect network traffic using passive agentless monitoring on IoT and OT devices. Sensors connect to a span port or network tap and immediately begin performing deep packet inspection (DPI) on IoT and OT network traffic.
Both components can be either installed on a dedicated appliance or on a VM.
DPI is achieved via the horizon component, which is responsible for analysing network traffic. The horizon component loads built-in dissectors and can be extended to add custom network protocol dissectors.
Both the management and the sensor share roughly the same code base, with configuration changes to fit the purpose of the machine. This is the reason why both machines are affected by most of the same vulnerabilities.
The most appealing attack surface exposed on both machines is the web interface, which allows controlling the environment in an easy way. The sensor additionally exposes another attack surface which is the DPI service (horizon) that parses the network traffic.
Defender for IoT is a product formerly known as CyberX, acquired by Microsoft in 2020. Looking around in the home directory of the CyberX user, researchers found the installation script and an archive containing the system’s encrypted files. Reading the script, they found the command that decrypts the archive file. The decryption key is shared across all installations.
After extracting the data, they found the sources for the web interface written in Python and got to work.
Azure Defender for IoT running with unpatched systems are affected. Since this product has many configurations, for example RTOS, which have not been tested, users of these systems can be affected as well.
A successful attack may lead to a full network compromise, since Azure Defender for IoT is configured to have a TAP (terminal access point) on the network traffic. Access to sensitive information on the network could open a number of sophisticated attacking scenarios that could be difficult or impossible to detect.
Sentinel disclosed its findings to Microsoft in June 2021, and Microsoft released a security advisory with patch details in December 2021.
While no evidence has been found of in-the-wild exploitation of these vulnerabilities, Sentinel further recommends revoking any privileged credentials deployed to the platform before the cloud platforms have been patched, and checking access logs for irregularities.
Cloud providers heavily invest in securing their platforms, but unknown zero-day vulnerabilities are inevitable and put users at risk. This is particularly concerning when it comes to IoT and OT devices that have little to no defences and depend entirely on these vulnerable platforms for their security posture. Cloud users, says Sentinel, should take a defence-in-depth approach to cloud security to ensure breaches are detected and contained, whether the threat comes from the outside or from the platform itself.




